 In a digital age where data is the new currency, safeguarding sensitive information is a top priority for organizations worldwide. ISO 27001 serves as a robust framework for achieving this goal. However, ensuring compliance with ISO 27001 and maintaining a strong Information Security Management System (ISMS) requires a structured approach.
In a digital age where data is the new currency, safeguarding sensitive information is a top priority for organizations worldwide. ISO 27001 serves as a robust framework for achieving this goal. However, ensuring compliance with ISO 27001 and maintaining a strong Information Security Management System (ISMS) requires a structured approach.
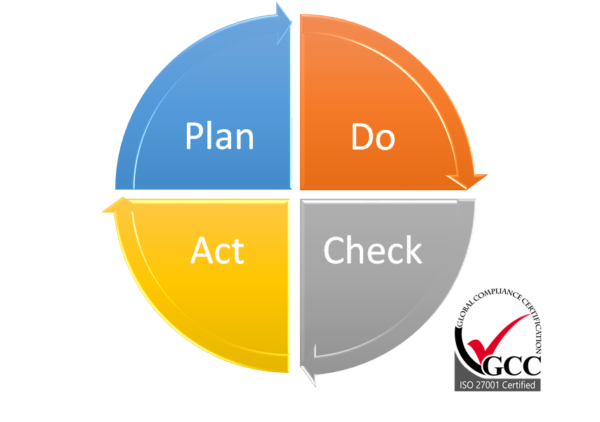
One such approach is the PDCA (Plan-Do-Check-Act) cycle, a simple yet powerful methodology. In this article, we’ll explore how the PDCA cycle can be effectively leveraged in the context of ISO 27001.
- Plan – Laying the Foundation
Defining Objectives and Scope:
The ‘Plan’ phase of the PDCA cycle begins with setting clear objectives for your ISMS. Set objectives should align with your organisation’s strategic goals. Are you aiming to protect sensitive customer data, comply with regulatory requirements, or enhance overall cybersecurity? Defining objectives provides a roadmap for your ISO 27001 journey.
Risk Assessment and Controls Selection:
A crucial step in the ‘Plan’ phase is conducting a comprehensive risk assessment. This process, helps identify potential threats and vulnerabilities unique to your organization. It serves as the foundation for selecting and implementing appropriate security controls.
- Do – Turning Plans into Action
Implementing Security Controls:
With a solid plan in place, you can then start implementation. In the ‘Do’ phase, you implement the security controls defined during the risk assessment. This may involve creating and enforcing policies, providing training to employees, deploying security software, or putting other protective measures in place. Involving your workforce, is pivotal, as employees play a vital role in your organization’s security posture.
Training and Awareness:
Information security is a collective responsibility. Therefore, ensuring that your staff is well-trained and aware of their roles and responsibilities regarding information security is crucial. An informed and vigilant workforce is your first line of defense against potential threats.
- Check – Continuous Monitoring and Review
Performance Monitoring:
The ‘Check’ phase revolves around continuous monitoring. Are the implemented controls effective? Are they achieving the desired outcomes? Regular performance monitoring helps identify areas that may require improvement. Measuring and analysing key performance indicators (KPIs) provides valuable insights into the health of your ISMS.
Incident Response:
In today’s threat landscape, security incidents are almost inevitable. Hence, it’s essential to establish a robust incident response plan. Preparedness is key to minimizing the impact of security incidents.
- Act – The Engine of Continuous Improvement
Continuous Improvement:
The ‘Act’ phase is the heart of the PDCA cycle. Based on the results of your monitoring and review, you take corrective and preventive actions. Addressing issues is essential, but proactively enhancing your processes, is equally critical. Continuous improvement ensures that your ISMS remains resilient and adaptable to emerging challenges.
Process Enhancement:
Cyber threats evolve rapidly, and your ISMS must evolve with them. Continuously improving your information security processes and controls is essential to adapt to evolving threats. This ensures that your organization remains secure and compliant with ISO 27001.
ISO 27001 certification is not a destination but a continuous journey toward information security excellence. The PDCA cycle provides a clear and effective framework for not only implementing ISO 27001 but also maintaining and improving your ISMS over time. By adhering to these four simple steps, organizations can build a robust information security posture that not only safeguards sensitive data but also adapts to the ever-changing threat landscape.